Chromecast and network namespaces
This is a follow-up to the post about OpenVPN for a single application.
I’ve finally found a way to access my Chromecast from a program running inside a network namespace! And it turns out it’s pretty easy to do.
With the setup I described in my last post, the isolated app has full access to the local network through the vpn1
interface. The only thing needed for the Chromecast to work is that the application must be able to discover the
Chromecast on the LAN.
The Chromecast discovery process uses mDNS (aka Bonjour, ZeroConf or whatever), which on Linux is usually handled by
Avahi. Basically, to discover Chromecasts on your LAN, you just have to do discover a device that publishes a
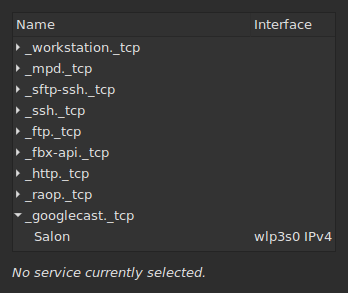
_googlecast._tcp PTR record. The human-friendly way to do this is to use avahi-discover-standalone. On my laptop, it
gives me the following result:
The issue is that inside the network namespace, the mDNS query will be sent on the vpn1 interface, but it won’t be
routed to the WLAN interface, so there won’t by any response:
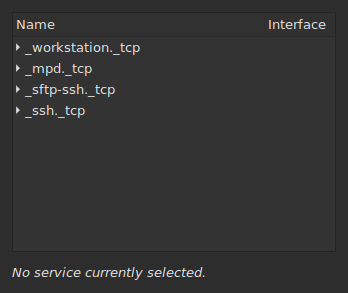
The only visible services are the ones from my laptop, and not the other ones from the WLAN.
However, there’s a very simple way to resolve this: it’s to configure Avahi to proxy all the mDNS queries to all the
available network interfaces! This feature is called “reflector”, and is a enabled by a one-line change in
/etc/avahi/avahi-daemon.conf:
[reflector]
enable-reflector=yes
Restart Avahi (systemctl restart avahi-daemon; reloading it is not enough here!) and try to run
avahi-discover-standalone again:
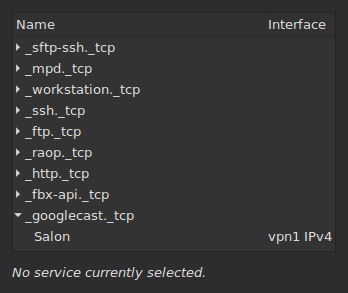
Much better! 😃 The device can now be discovered, and applications running in the network namespace can therefore use it at will.
Thanks to Joel Knight for the tip!
Comments
Join the conversation by sending an email. Your comment will be added here and to the public inbox after moderation.